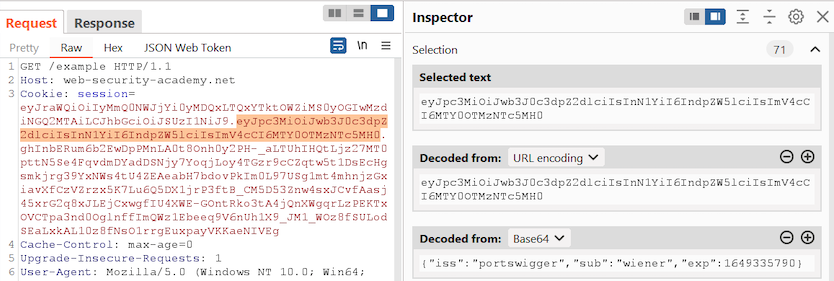
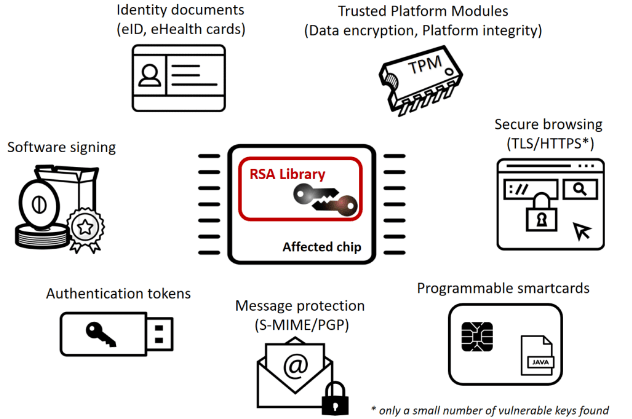
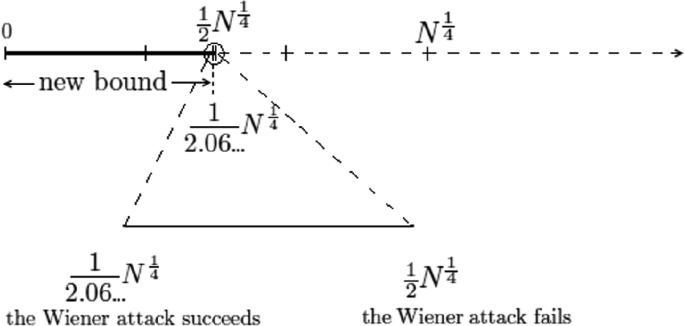
RSA: Continued Fractions — The Wiener Attack | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
RSA: Continued Fractions — The Wiener Attack | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
![PDF] The Return of Coppersmith's Attack: Practical Factorization of Widely Used RSA Moduli | Semantic Scholar PDF] The Return of Coppersmith's Attack: Practical Factorization of Widely Used RSA Moduli | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0b978f224b8520c8e3d9b2eb55431262fcb16c05/13-Table4-1.png)
PDF] The Return of Coppersmith's Attack: Practical Factorization of Widely Used RSA Moduli | Semantic Scholar