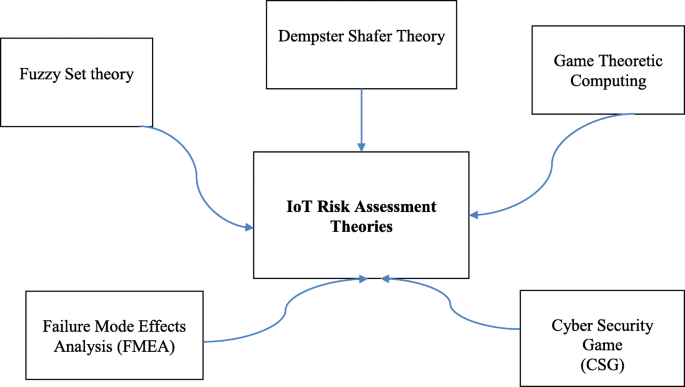
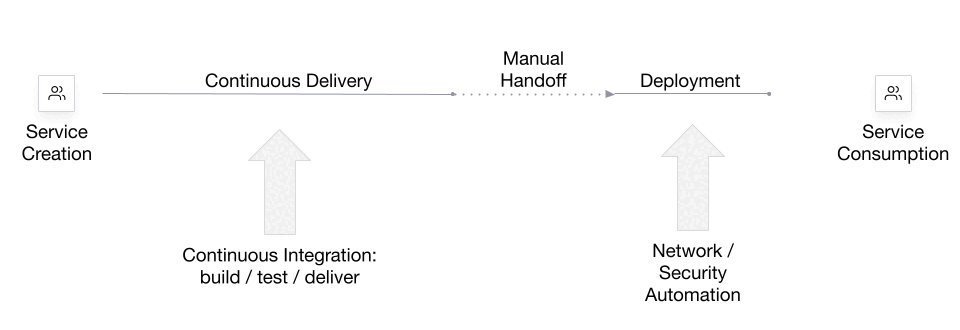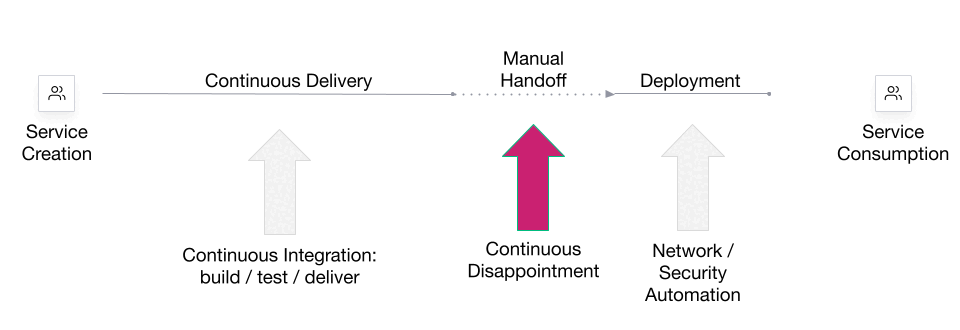
Systematic threat assessment and security testing of automotive over-the-air (OTA) updates - ScienceDirect

ATC/DME test set for engineering, validation, test applications introduced by Cobham AvComm | Military Aerospace

Risk Governance of Emerging Technologies Demonstrated in Terms of its Applicability to Nanomaterials - Isigonis - 2020 - Small - Wiley Online Library

PDF) Identifying Potentially Flawed Items in the Context of Small Sample IRT Analysis | Panagiotis Fotaris, Athanasios Manitsaris, Ioannis Mavridis, and Theodoros Mastoras - Academia.edu

Systematic threat assessment and security testing of automotive over-the-air (OTA) updates - ScienceDirect

Systematic threat assessment and security testing of automotive over-the-air (OTA) updates - ScienceDirect
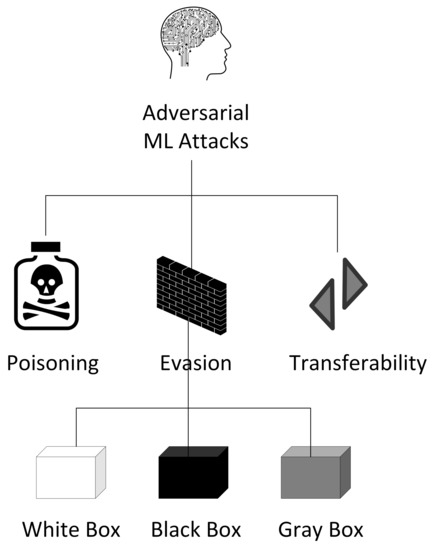
JCP | Free Full-Text | Functionality-Preserving Adversarial Machine Learning for Robust Classification in Cybersecurity and Intrusion Detection Domains: A Survey | HTML
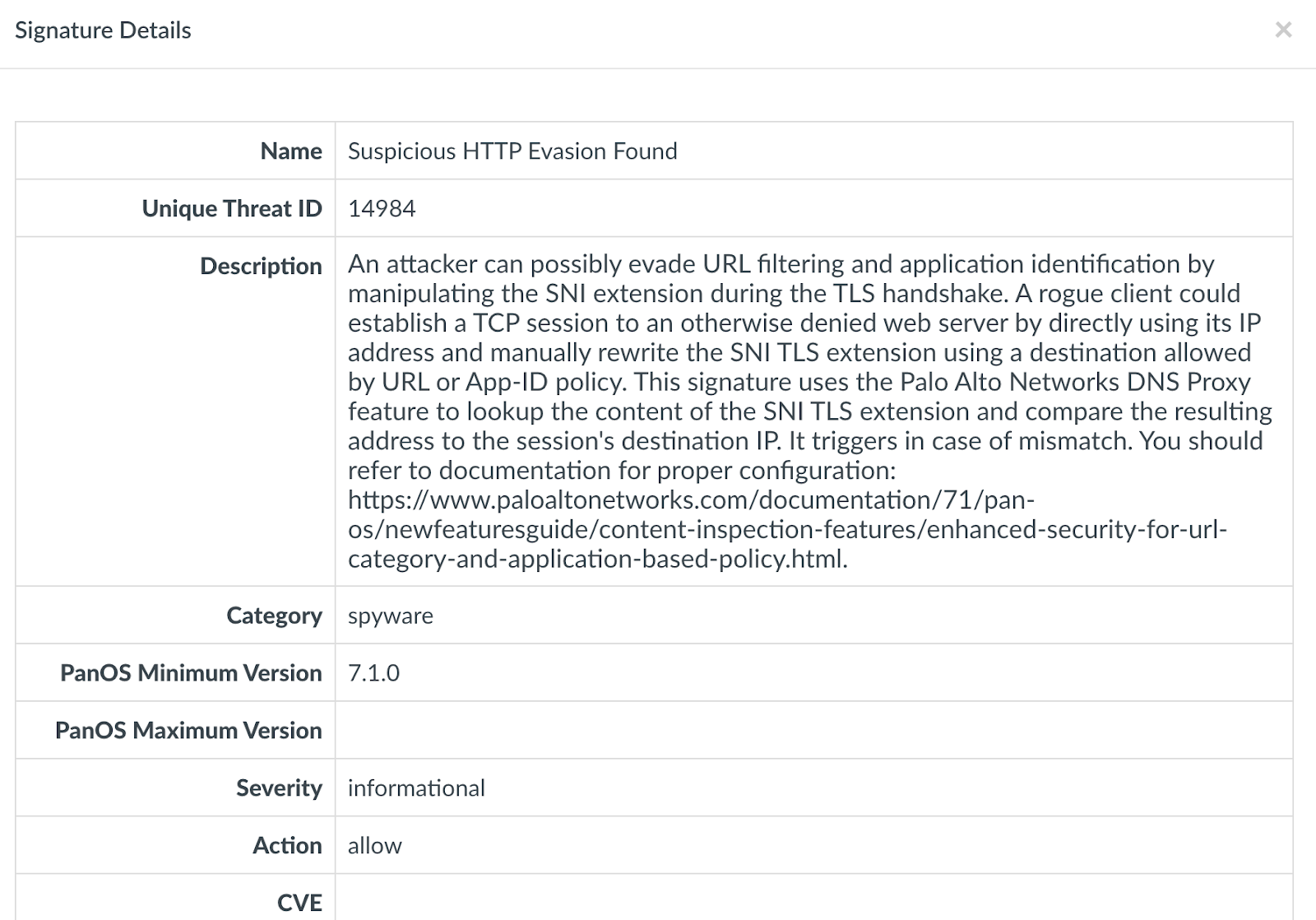
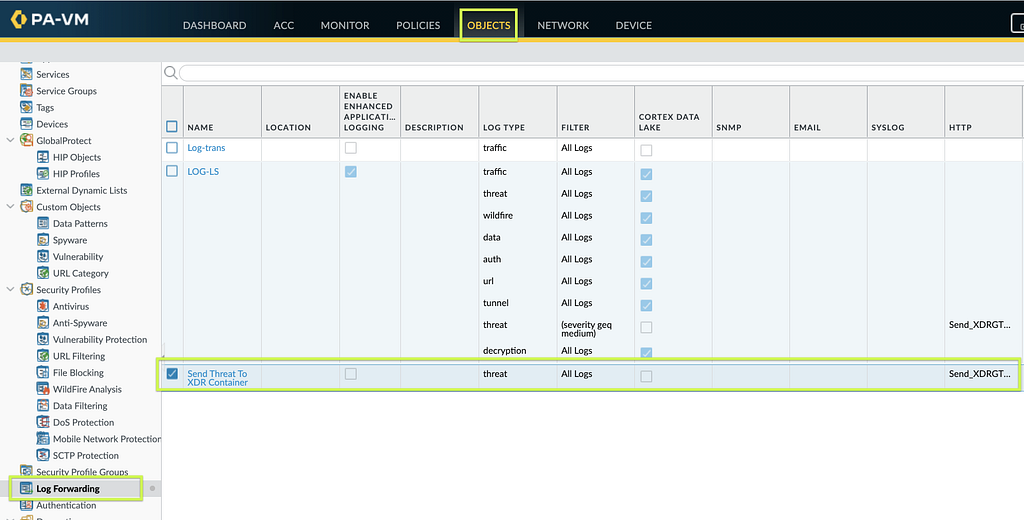
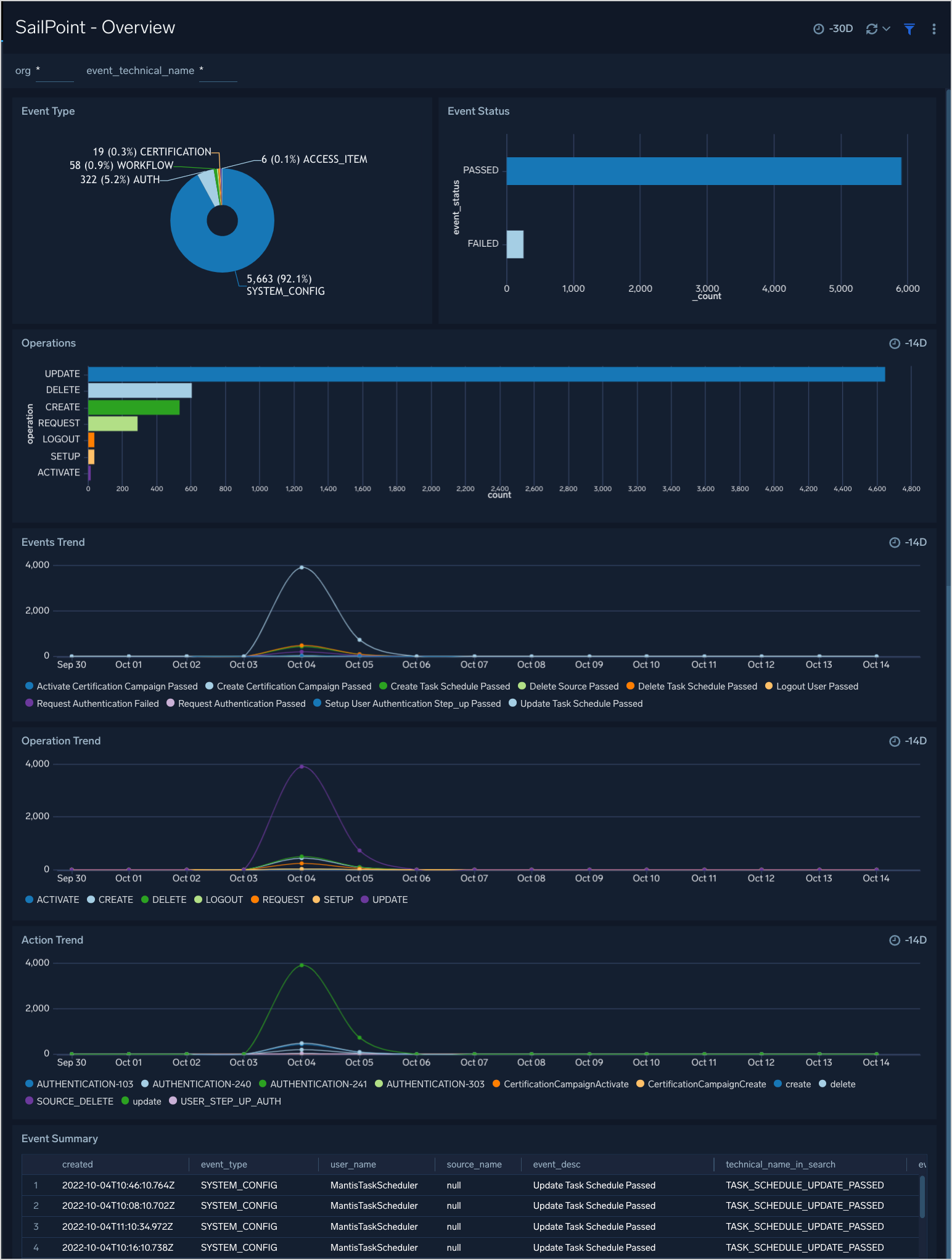
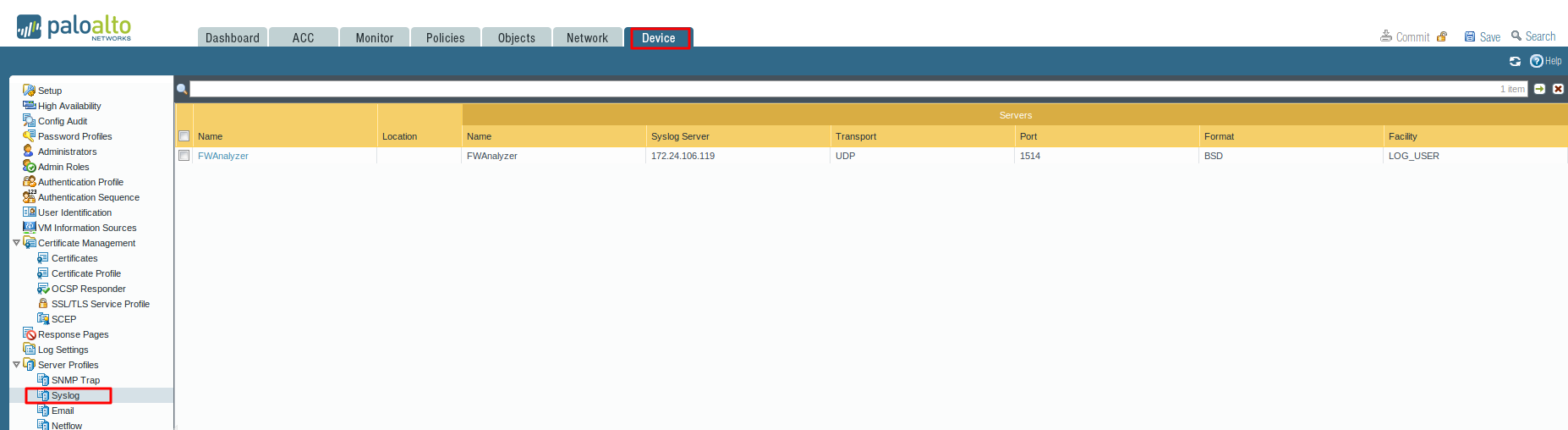
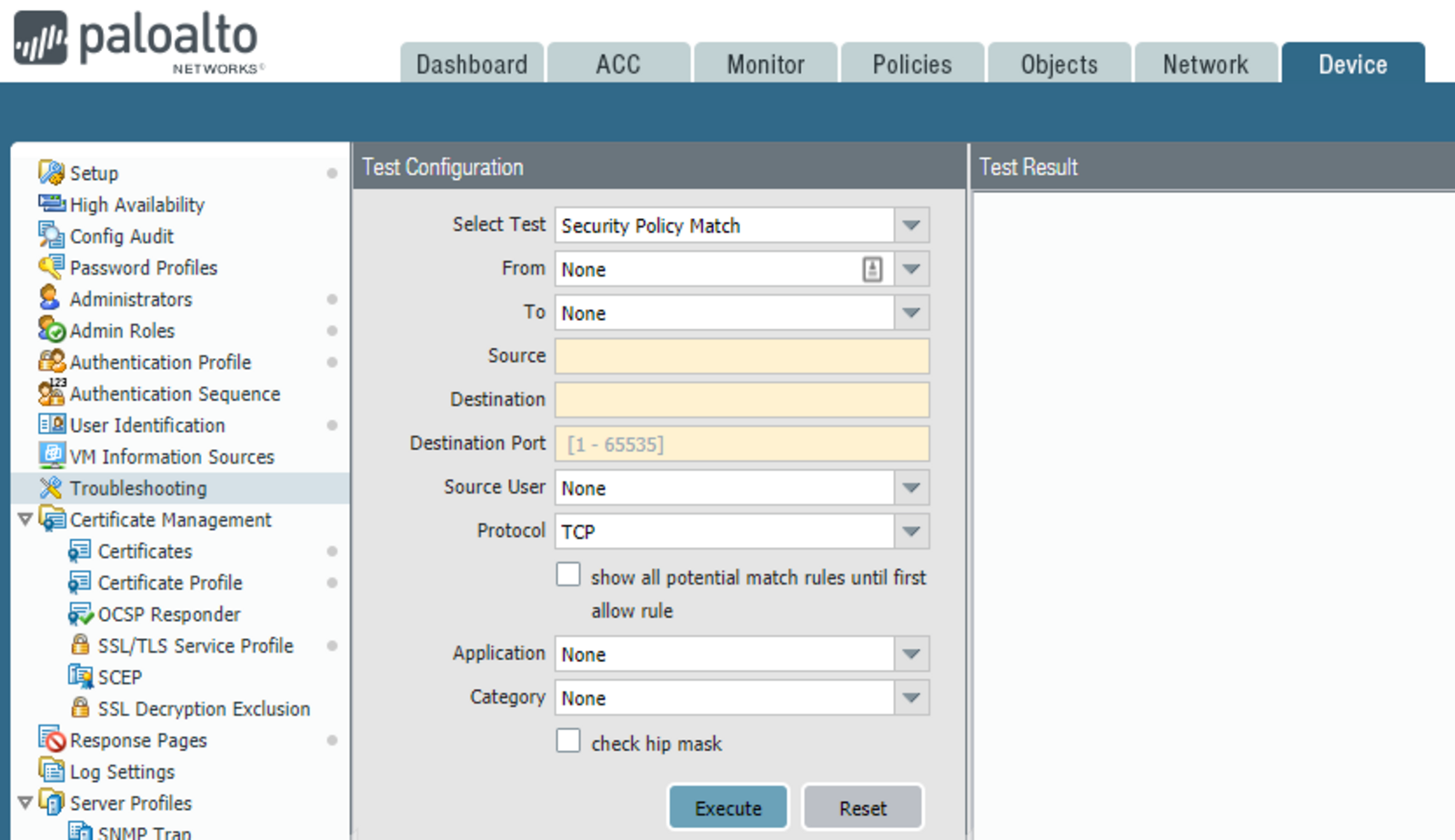
Mitigate Vulnerabilities Through Proper Application of Threat P... - Knowledge Base - Palo Alto Networks