Read the following list: Open ppsspp, start tekken 6, press Esc key and select "Game Settings". 2… | Playstation, Playstation portable, Xbox console
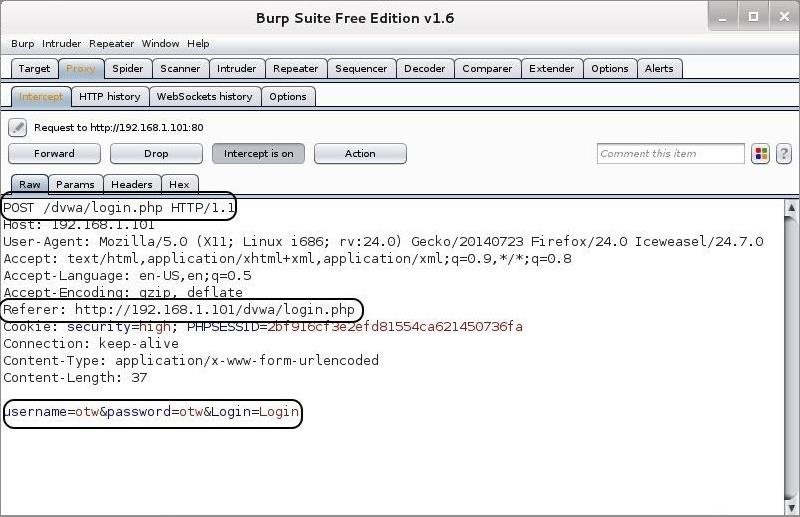
Hack Like a Pro: How to Crack Online Web Form Passwords with THC-Hydra & Burp Suite « Null Byte :: WonderHowTo