The Model Of Quantifying Information Security With Cobit 5 Matrix In Indonesia Higher Education | Semantic Scholar

The HITRUST Shared Responsibility Matrix: The Key to Secure Adoption of Cloud Technologies - HITRUST Alliance

Matrix of the Internet Security Framework. The table shows security... | Download Scientific Diagram
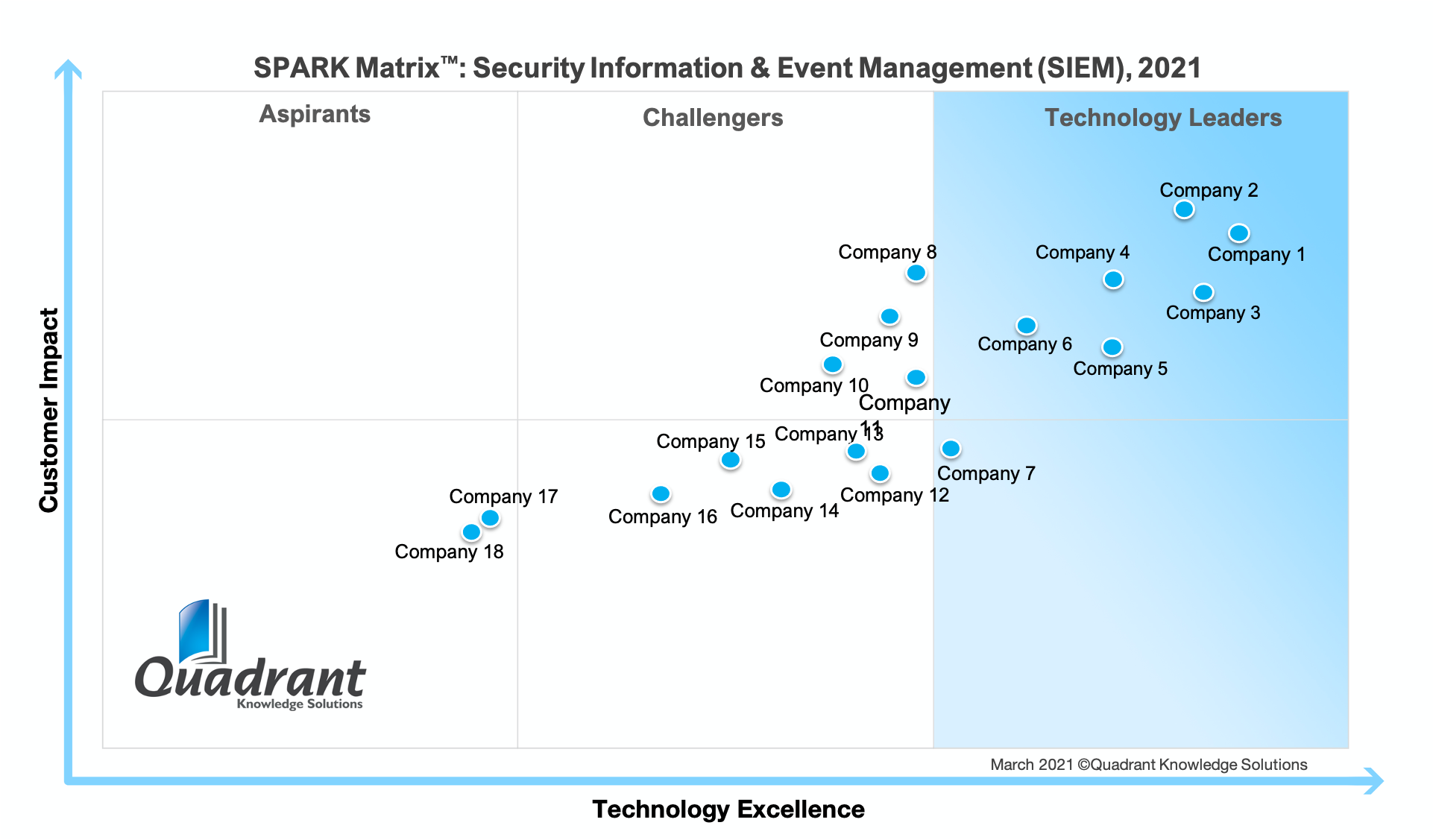
SPARK Matrix™: Security Information and Event Management (SIEM), 2021 - Quadrant Knowledge Solutions SPARK Matrix™: Security Information and Event Management (SIEM), 2021
Skill Matrix Table Identifying Technical Security And Transaction Processing | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas