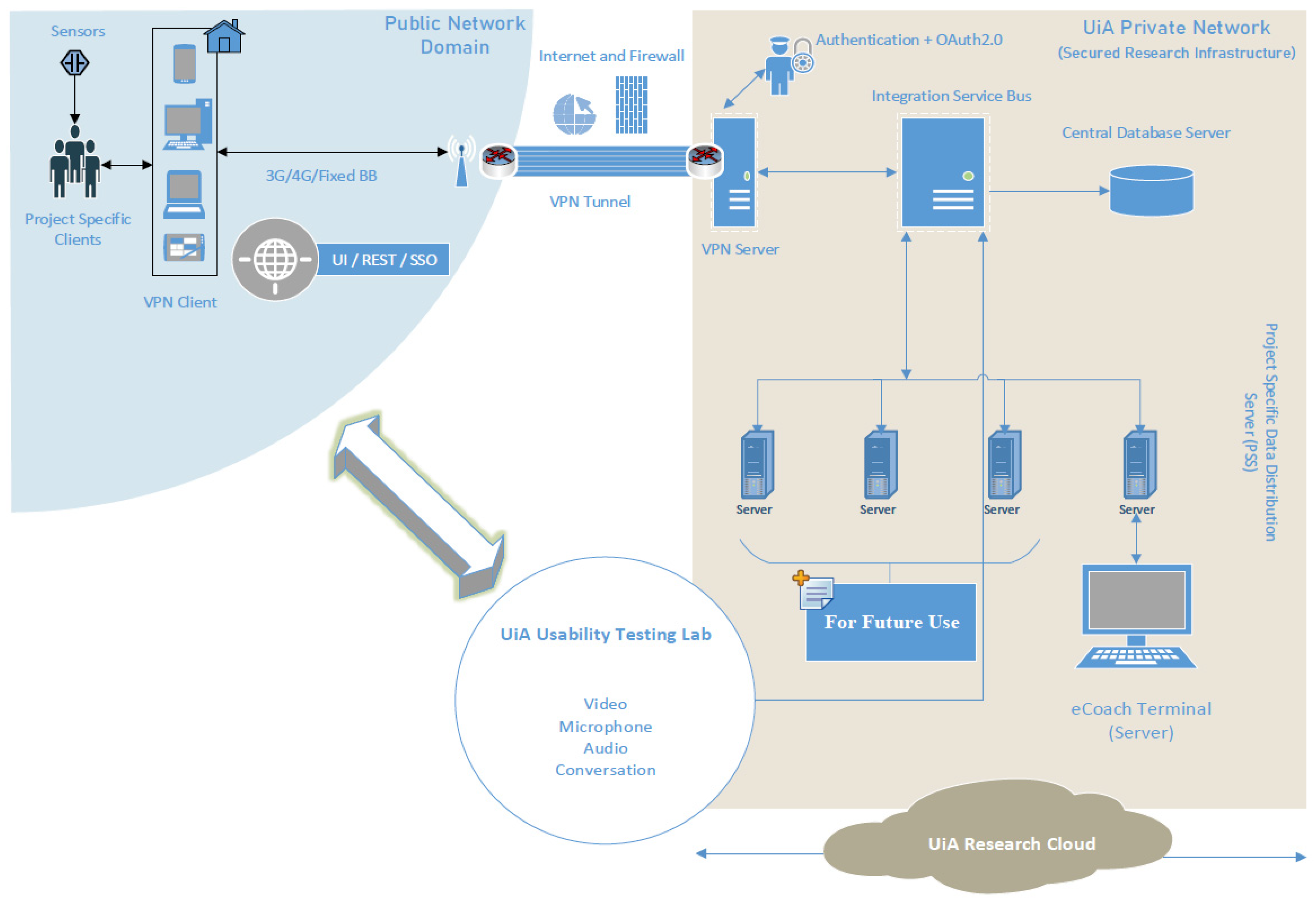
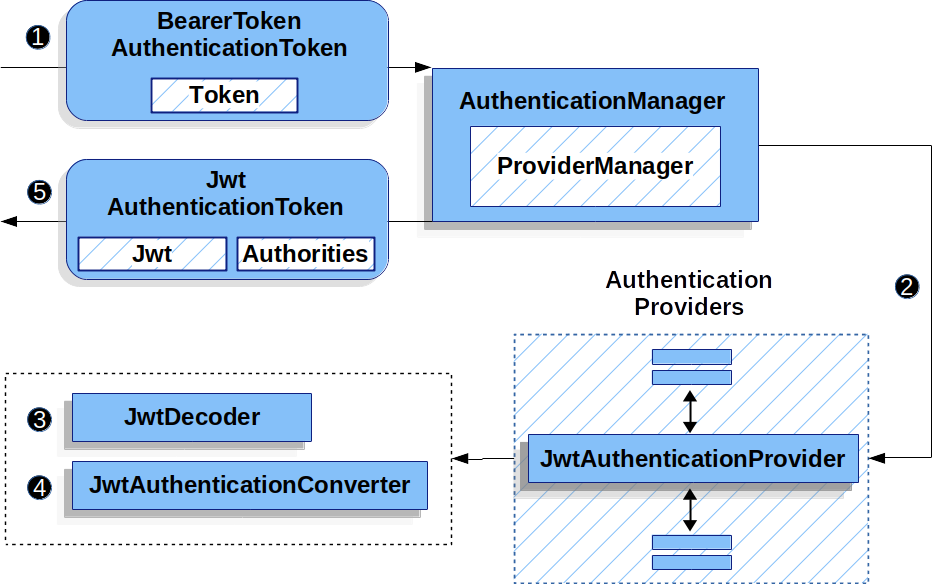
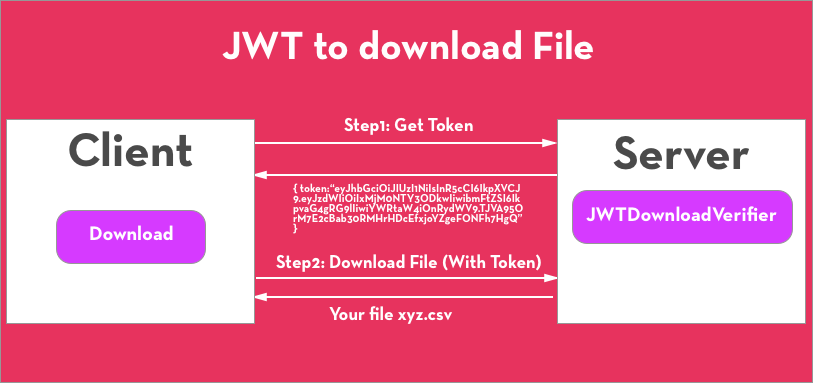
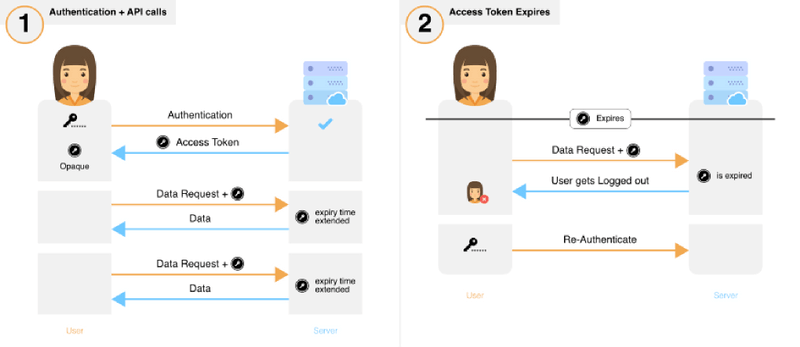
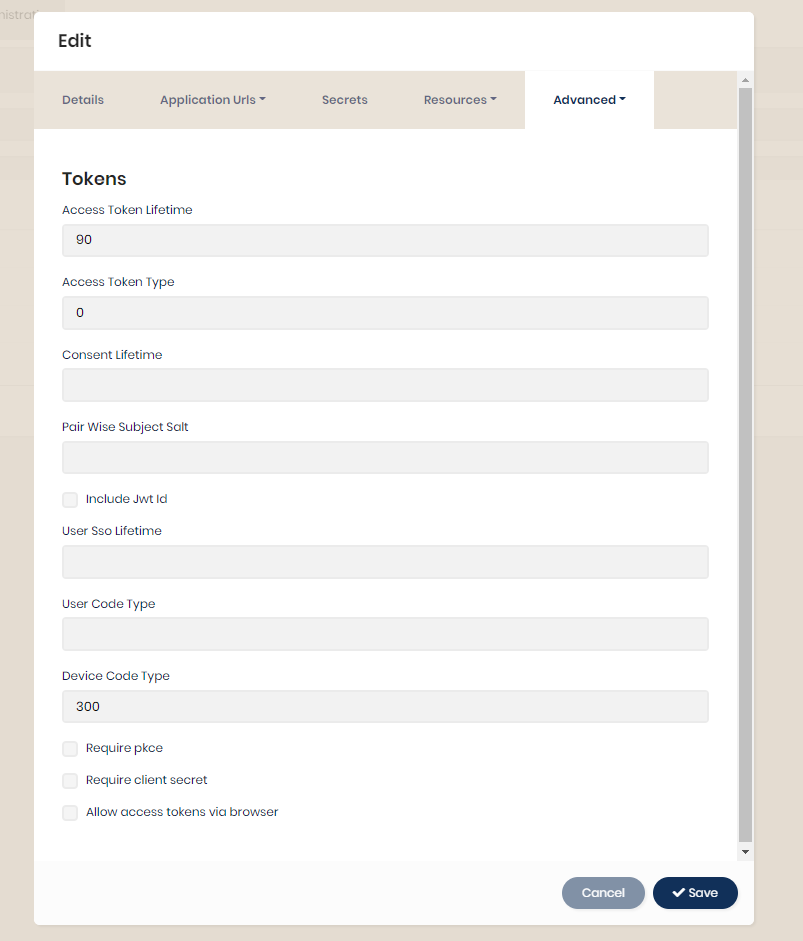
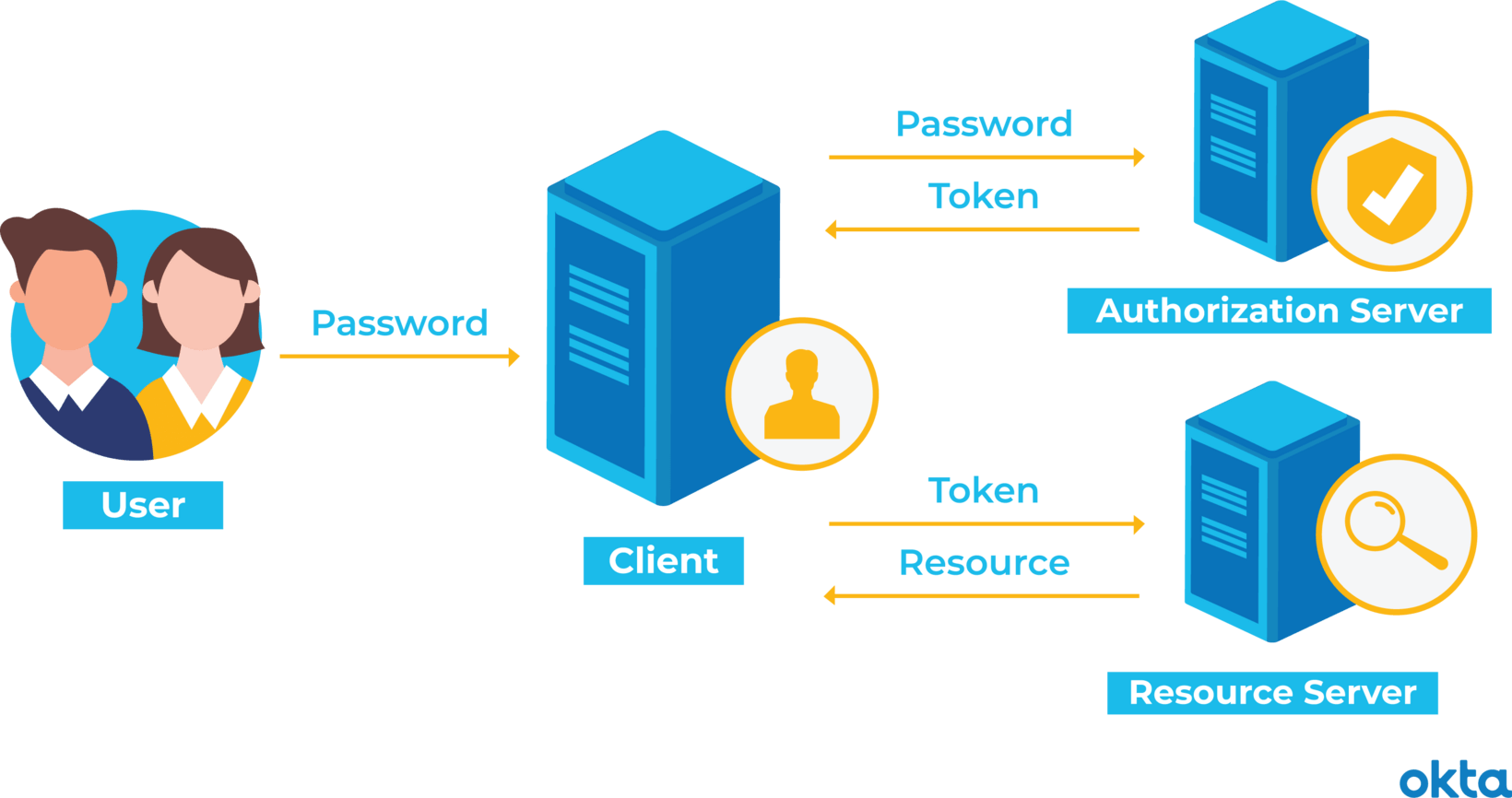
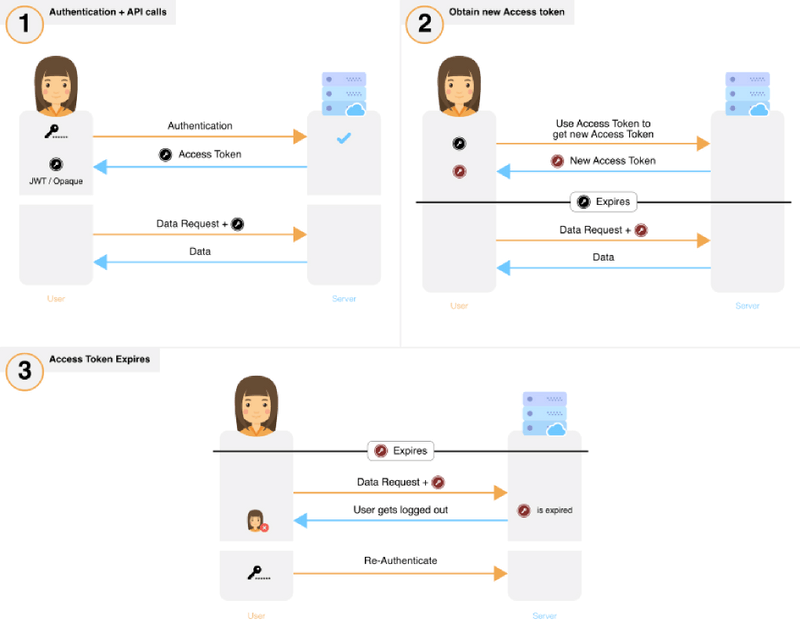
How to Sign-In with Google in Angular and use JWT based .NET Core API Authentication (RSA) | by Christian Zink | Level Up Coding

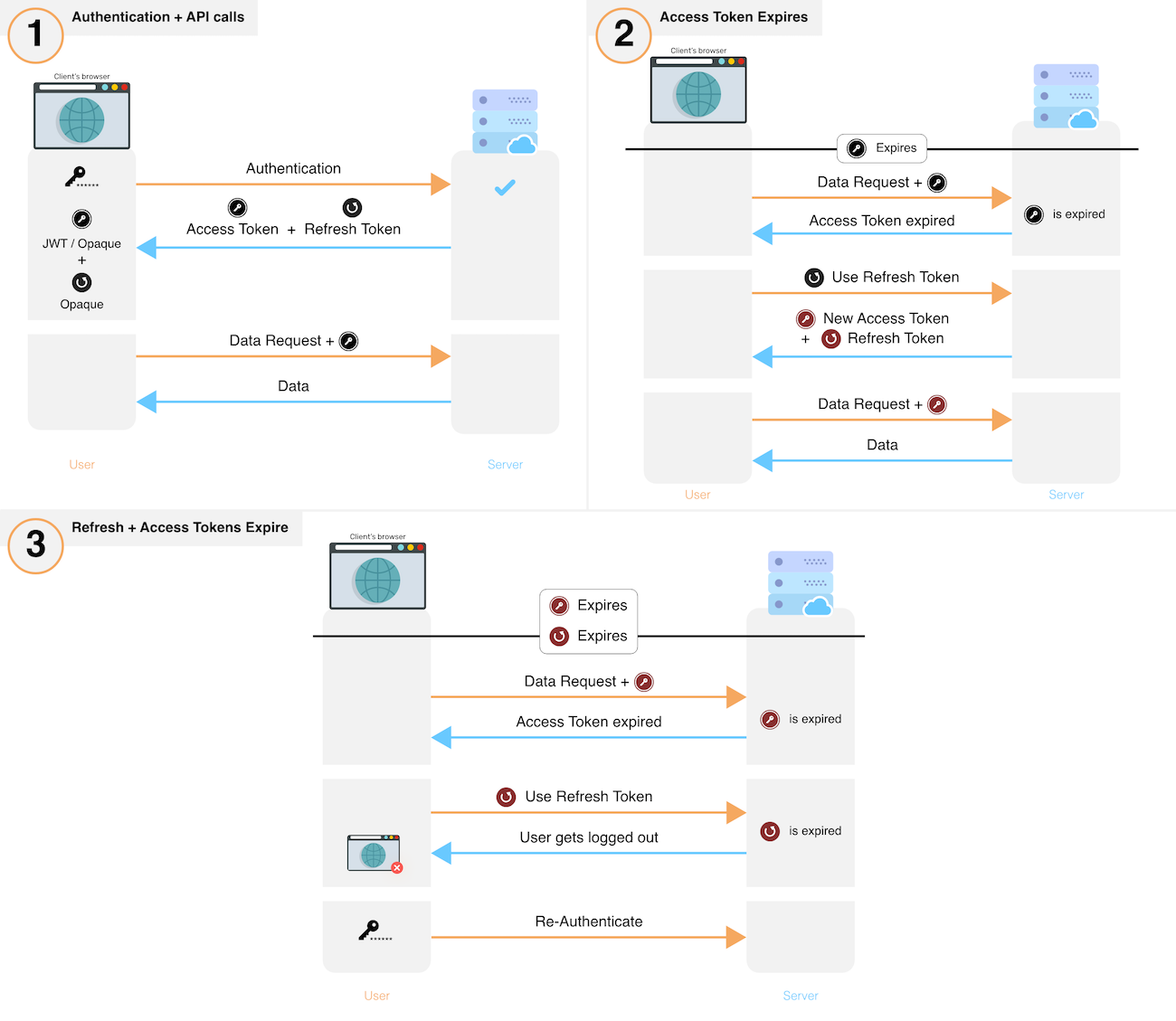
How to create an Authentication System using JWT and Node.js | by Ram Potabatti | JavaScript in Plain English
![4. Securing the Login with OAuth 2 and OpenID Connect - Identity and Data Security for Web Development [Book] 4. Securing the Login with OAuth 2 and OpenID Connect - Identity and Data Security for Web Development [Book]](https://www.oreilly.com/api/v2/epubs/9781491937006/files/assets/idds_0402.png)
4. Securing the Login with OAuth 2 and OpenID Connect - Identity and Data Security for Web Development [Book]