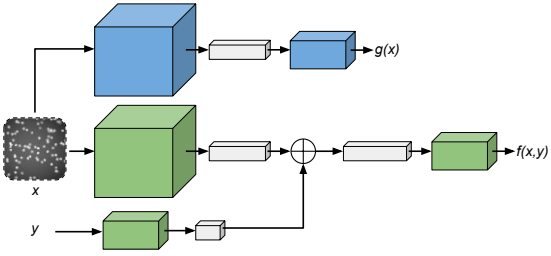
Remote Sensing | Free Full-Text | A Joint Denoising Learning Model for Weight Update Space–Time Diversity Method | HTML
Full article: The 2007 cyber attacks against Estonia and international law on the use of force: an informational approach

Electronics | Free Full-Text | A Novel Data-Driven Specific Emitter Identification Feature Based on Machine Cognition | HTML

Frontiers | A Feature Tensor-Based Epileptic Detection Model Based on Improved Edge Removal Approach for Directed Brain Networks

Genetic perceptual shaping: Utilizing cover image and conceivable attack information during watermark embedding - ScienceDirect
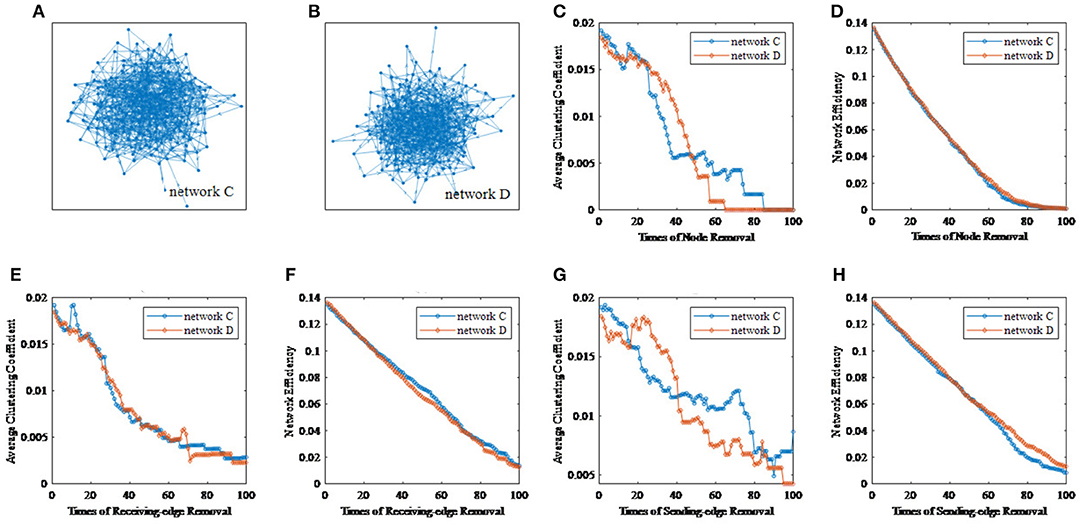
Frontiers | A Feature Tensor-Based Epileptic Detection Model Based on Improved Edge Removal Approach for Directed Brain Networks

A Hybrid robust watermarking system based on discrete cosine transform, discrete wavelet transform, and singular value decomposition - ScienceDirect