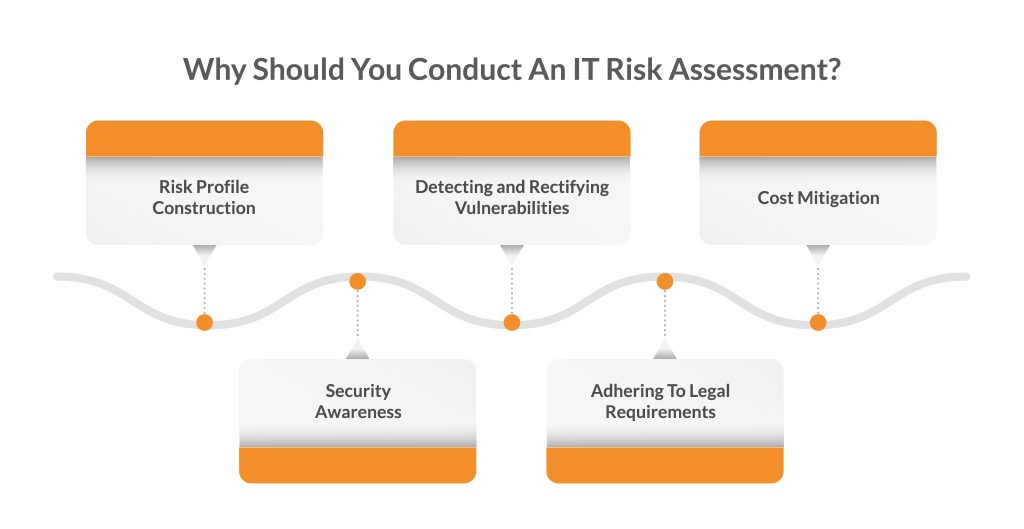
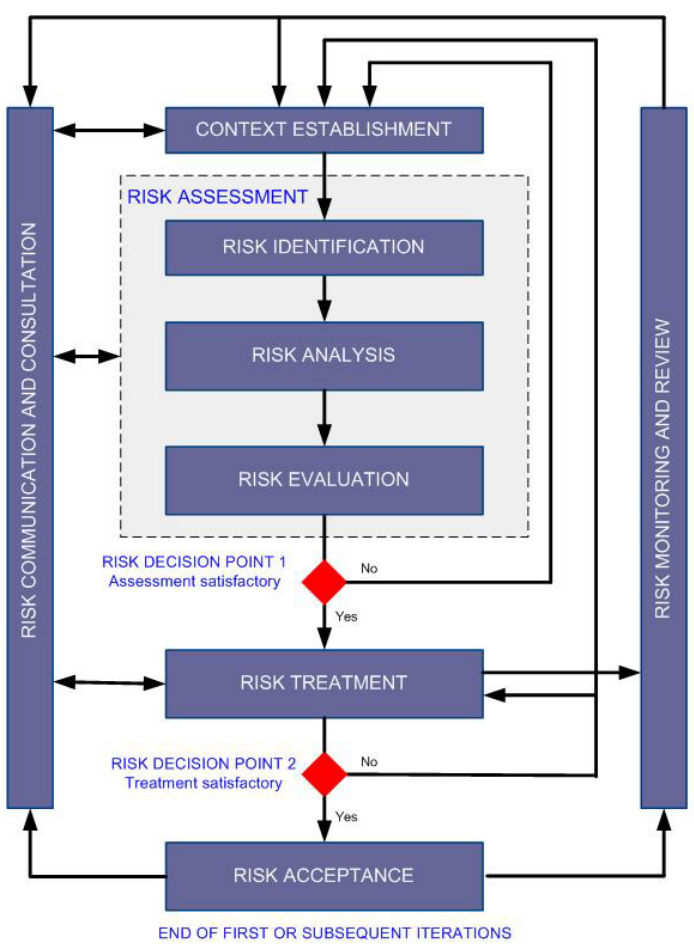
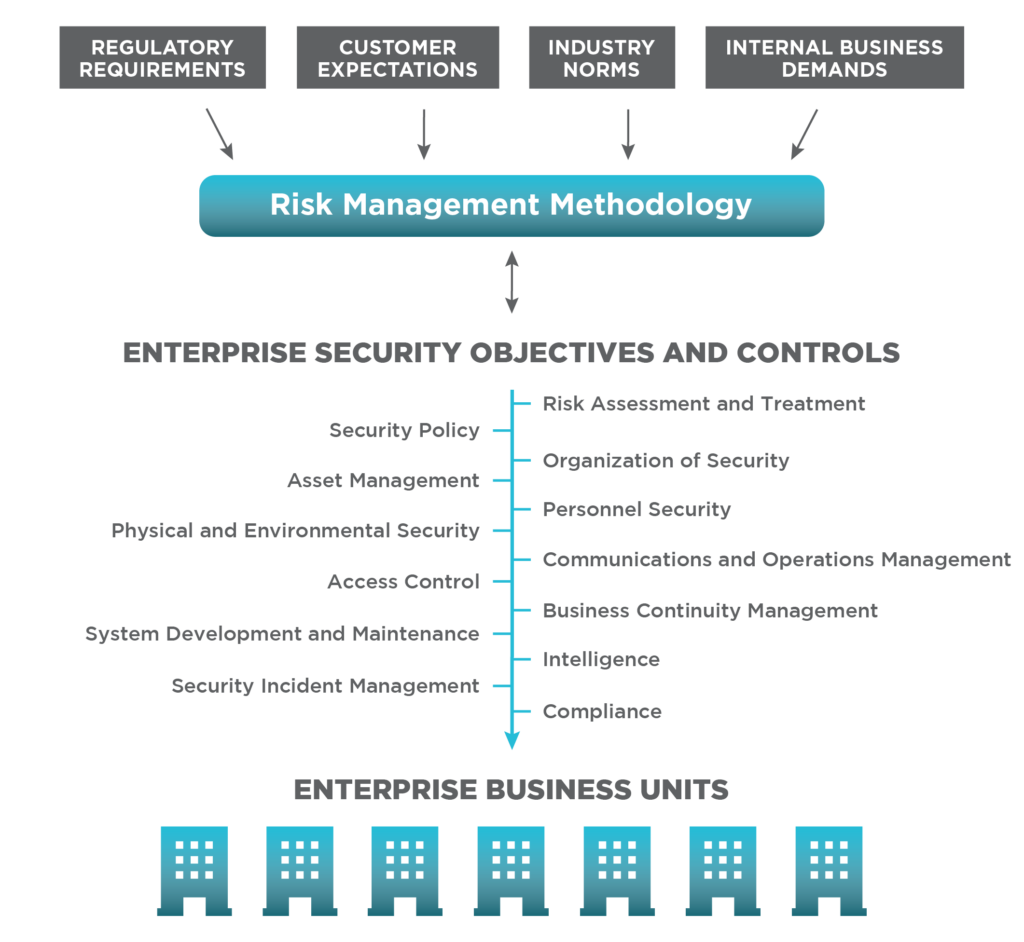
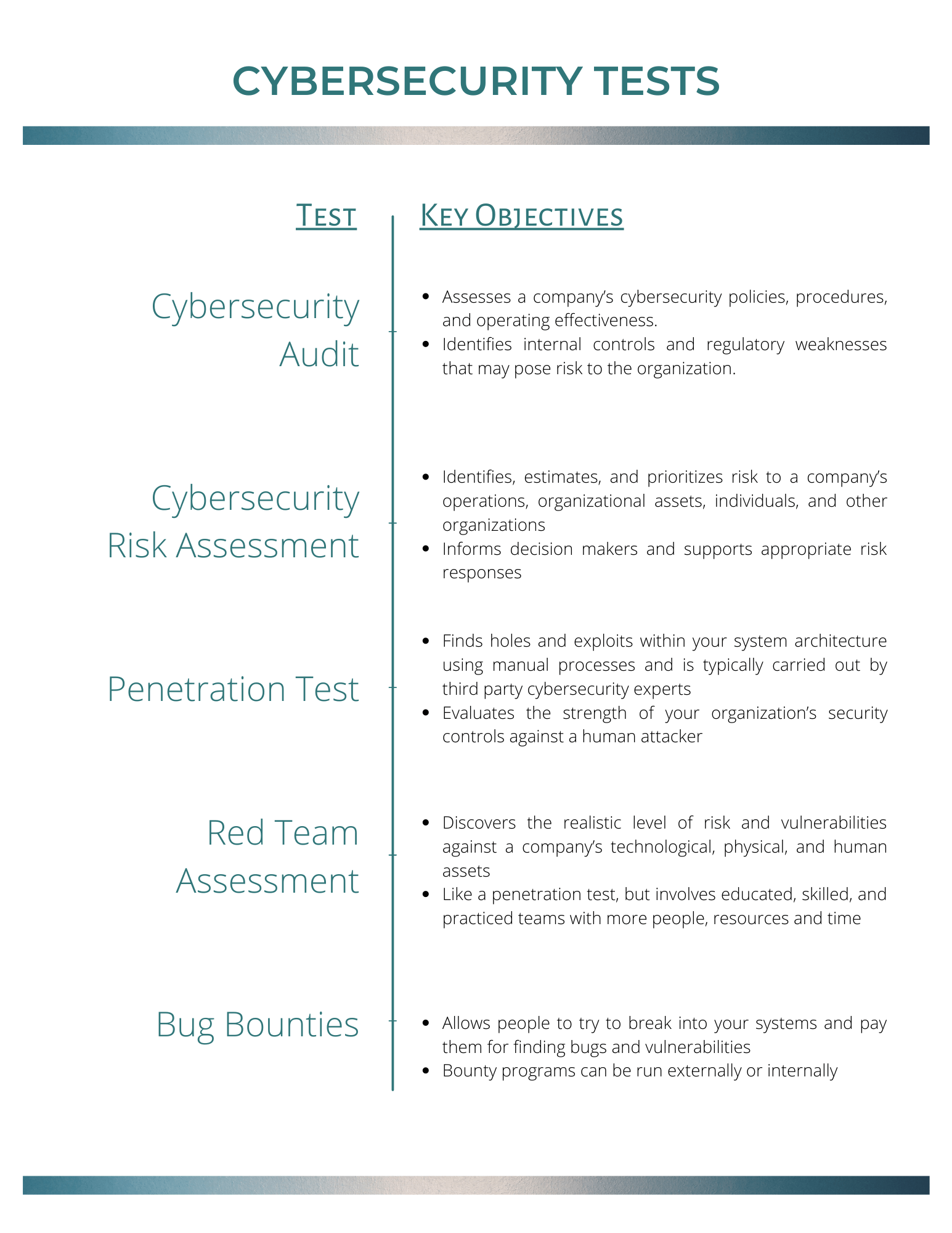
Criteria for Selecting a Risk Assessment Methodology | by Eric Vanderburg | Security Thinking Cap | Medium

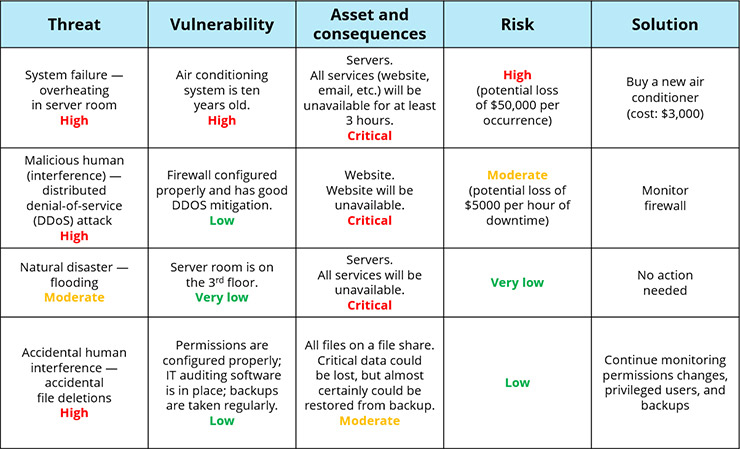
Cybersecurity Risk Assessment Chart For Organization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates
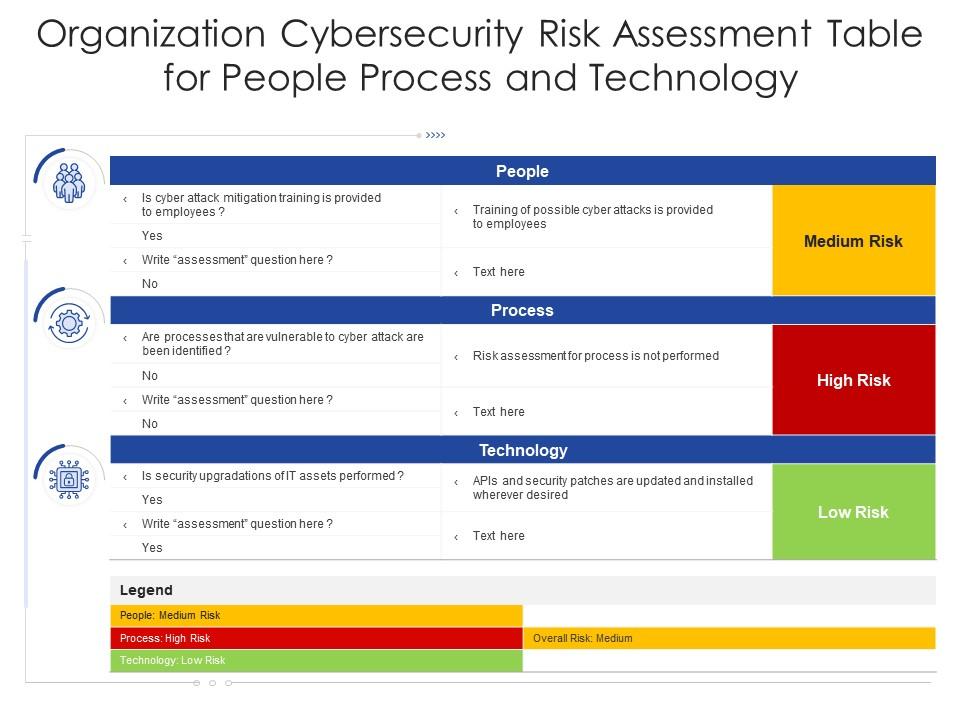
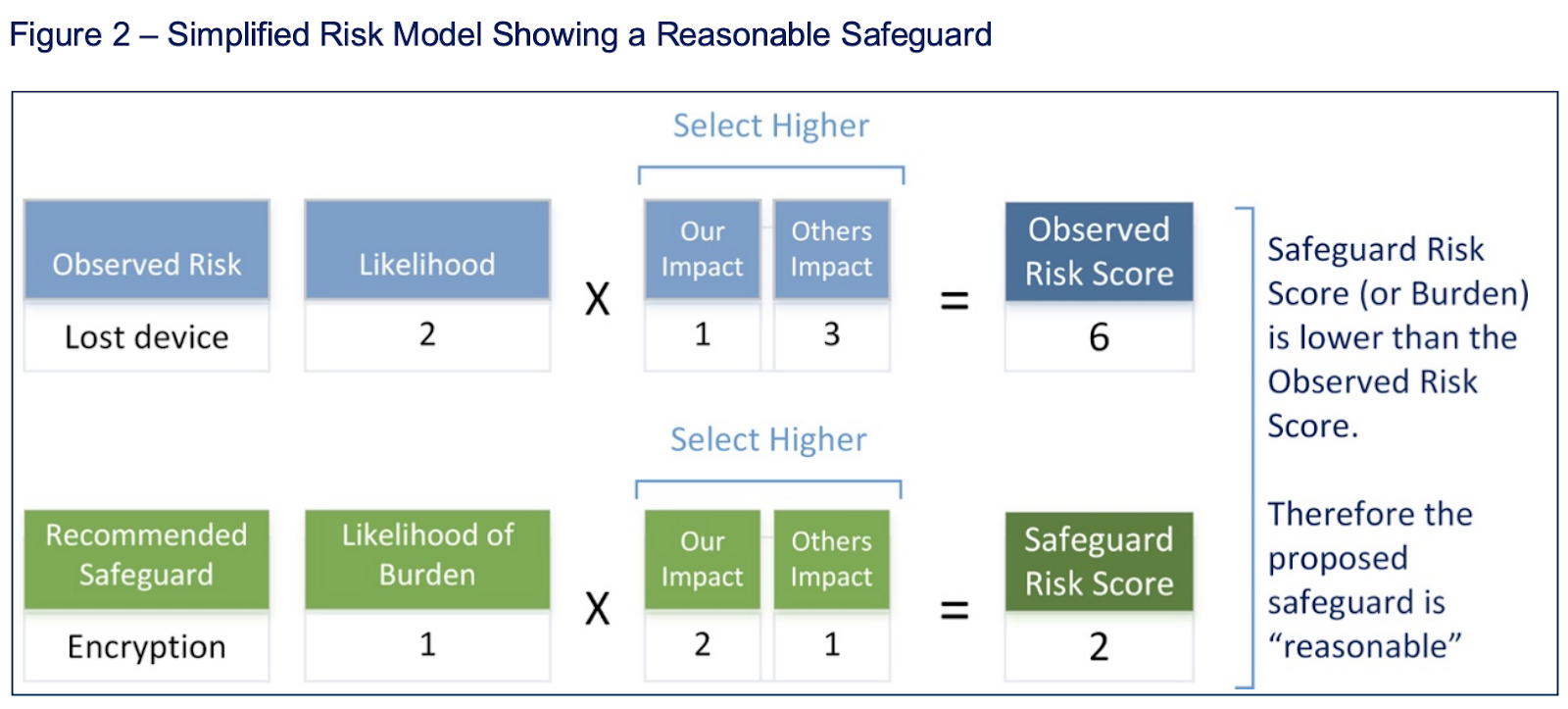
Organization Cybersecurity Risk Assessment Table For People Process And Technology | Presentation Graphics | Presentation PowerPoint Example | Slide Templates