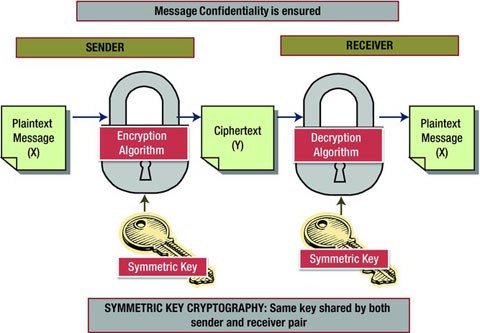
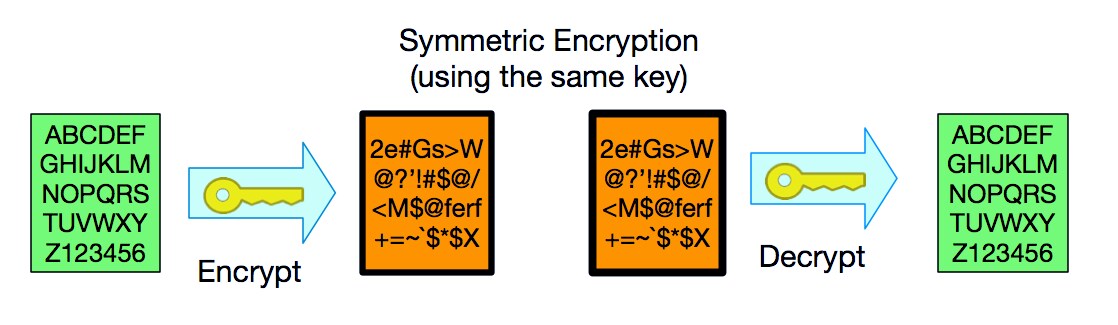
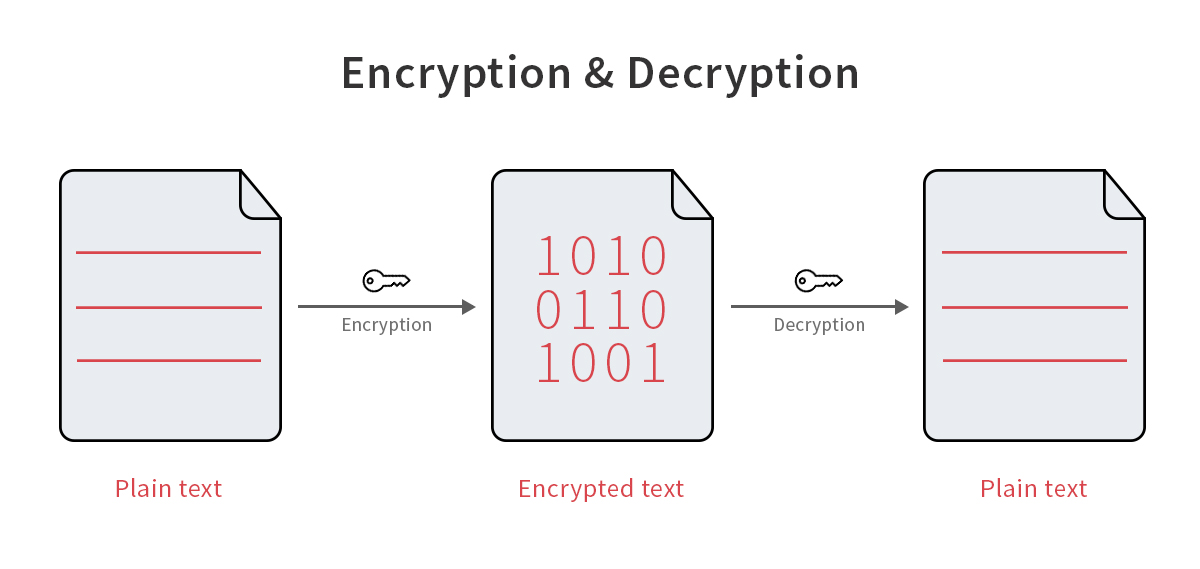
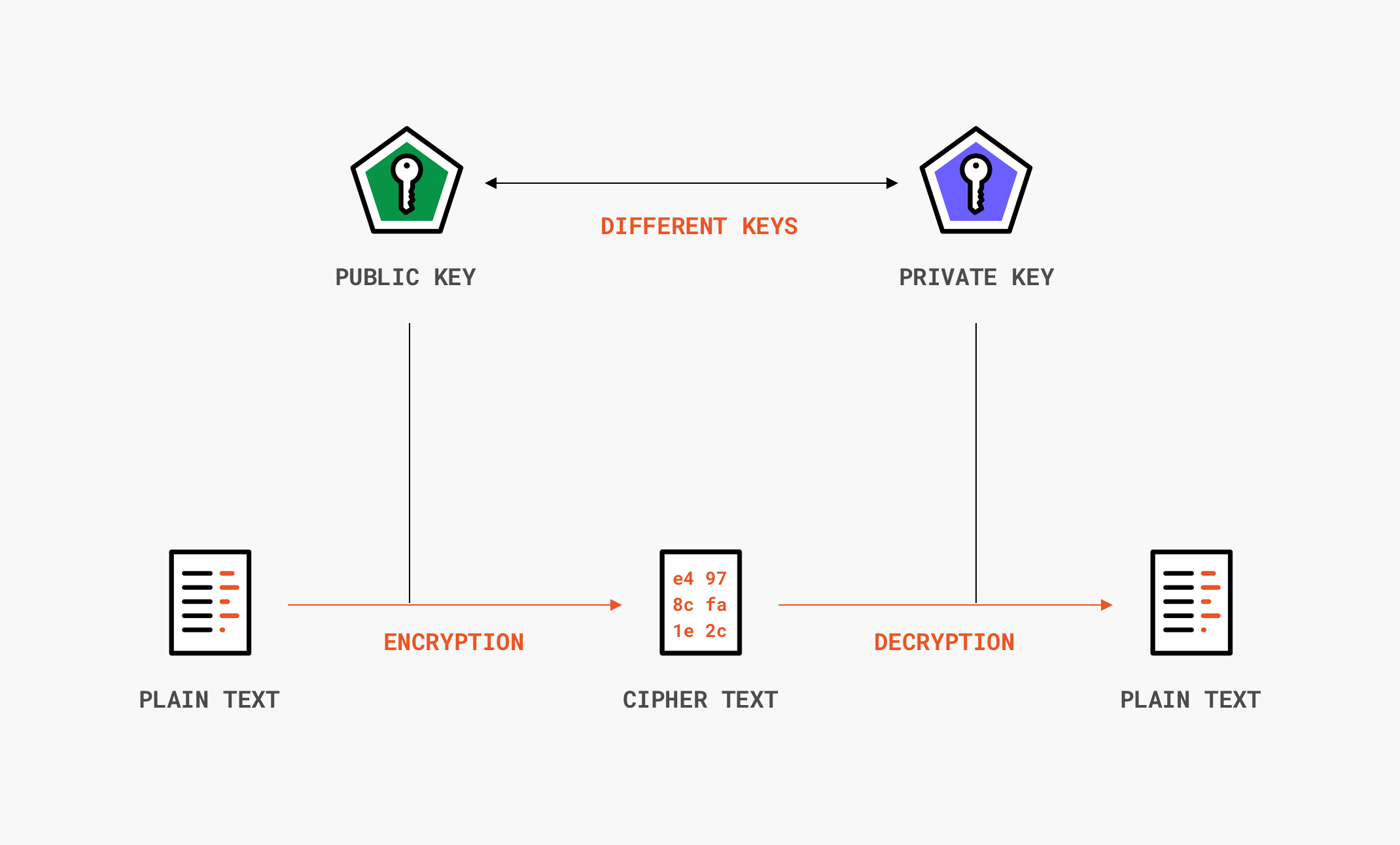
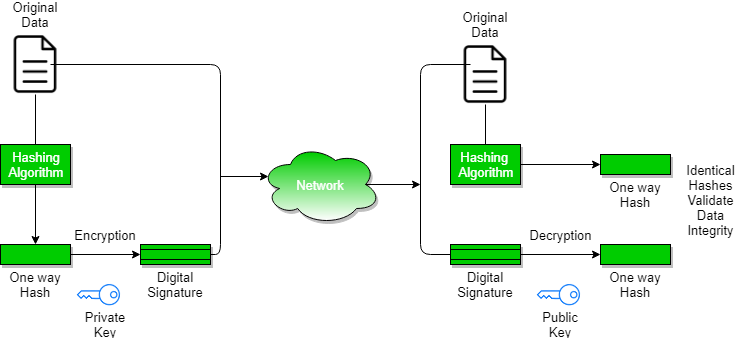
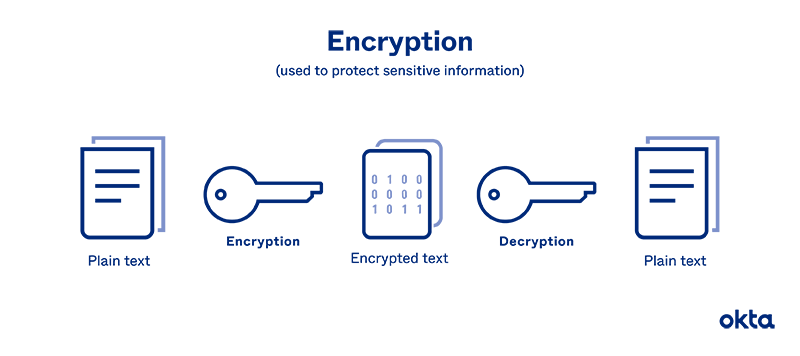
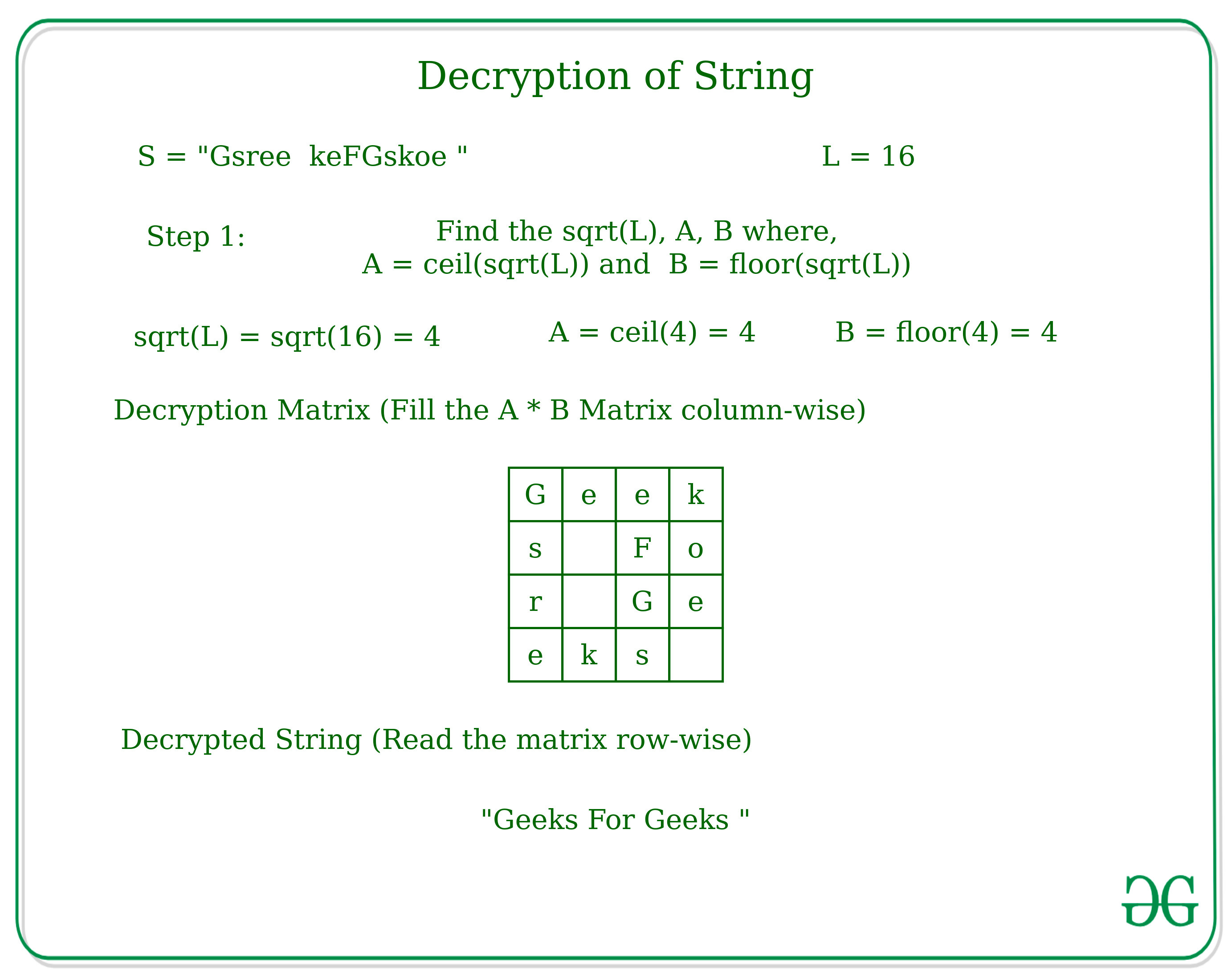
PDF) Information Security: Text Encryption and Decryption with poly substitution method and combining the features of Cryptography

Implementing Secure RSA Cryptosystems Using Your Own Cryptographic JCE Provider - SciAlert Responsive Version


![4. Keys, Addresses, Wallets - Mastering Bitcoin [Book] 4. Keys, Addresses, Wallets - Mastering Bitcoin [Book]](https://www.oreilly.com/api/v2/epubs/9781491902639/files/images/msbt_0411.png)