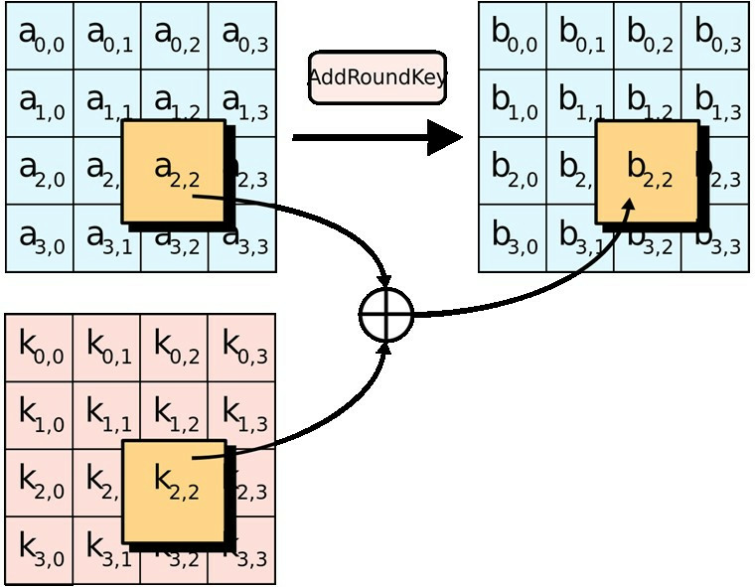
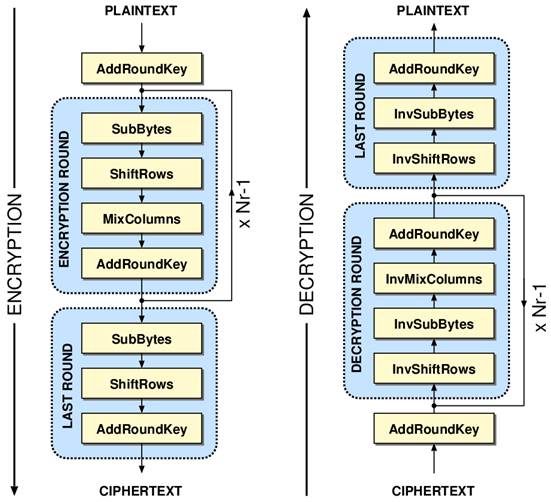
AES Encryption Function ontools | AES Encryption Free Online Tool Supports 128 192 256 Bits... | #1 BEST - AES Encryption Online - ᐈ AES Encryption and Decryption Online Tool | Online AES Encryption and Decryption function ontools
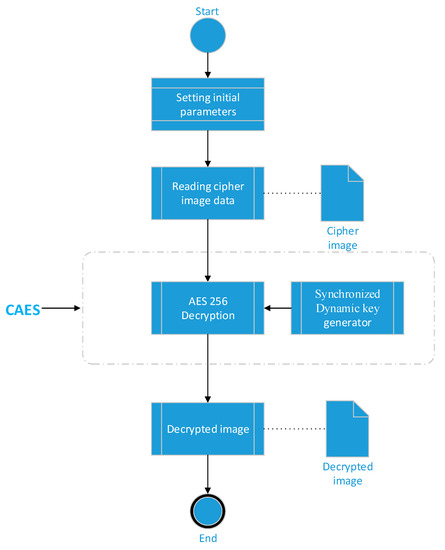
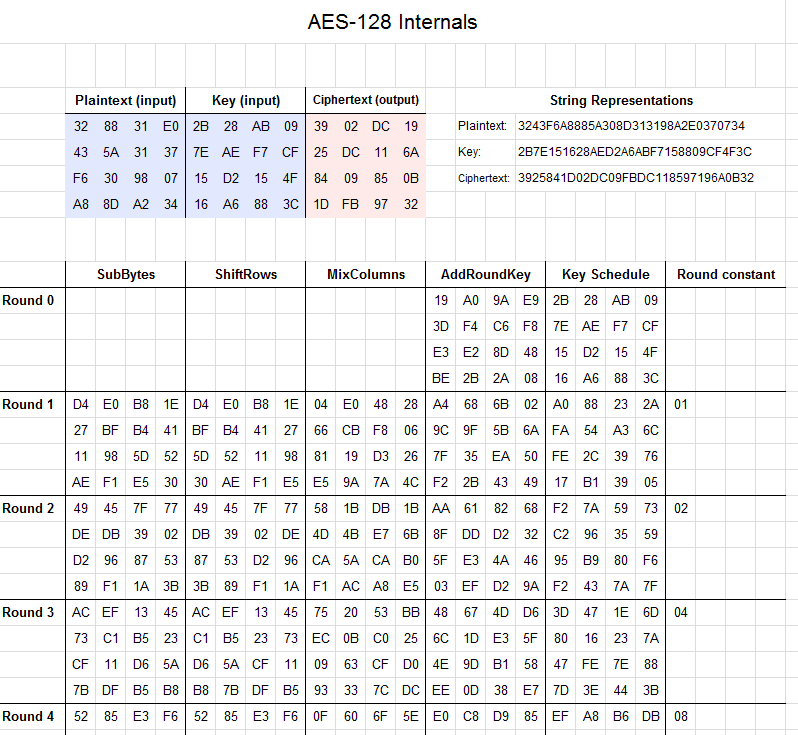
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm | HTML

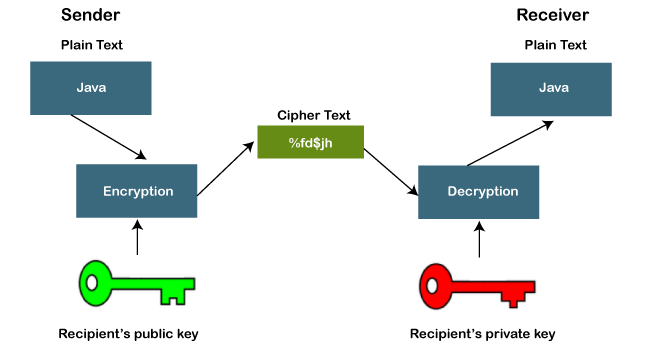
A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention

A Comparison of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish for Guessing Attacks Prevention

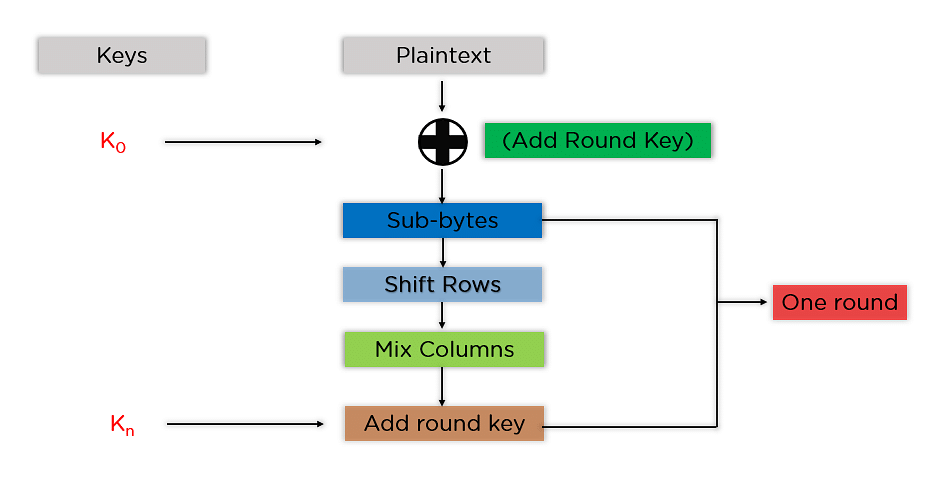
A lightweight AES algorithm implementation for encrypting voice messages using field programmable gate arrays - ScienceDirect